Hello everyone in the trading and cryptocurrency investment community! If you have ever had an interest in earning quick and effortless money through cryptocurrency trading, I am about to unveil a tremendous secret: the utilization of “crypto pump signals” is responsible for a significant portion of traders’ financial gains. To explain it in simpler words, when you possess privileged information regarding digital coins that are on the brink of experiencing a substantial price surge, you procure the required cryptocurrency and patiently await its value to escalate. At that point, you then sell the previously acquired digital token at a significantly higher price, resulting in enormous profits.
All of these events occur rapidly, resulting in profitable information being delivered daily. If you lack the necessary expertise, this article will guide you on how and where to access both paid and free information regarding upcoming altcoin pumps on the Binance exchange, as well as how to benefit from this advantageous insider knowledge.

Crypto Pump Signals for Binance is an exceptional initiative that supplies traders and investors with valuable details regarding upcoming cryptocurrency pumps. Through the utilization of a Telegram channel and artificial intelligence capabilities, this project presents new chances for generating substantial profits in the short-term.
Investors can gain an edge in the digital market with the trading signals offered by the “Crypto Pump Signals for Binance” project. These signals provide advance information about cryptocurrency pumps, allowing investors to anticipate price changes and make successful trades.
The project’s artificial intelligence technology ensures that information is analyzed quickly and accurately. By processing vast amounts of data, algorithms identify the most promising trading opportunities. This means that Crypto Pump Signals for Binance offers reliable signals to help investors make informed decisions when investing in cryptocurrencies. For more details on how artificial intelligence technology is used to predict short-term fluctuations in cryptocurrency prices, please refer to the end of this article.
One of the primary benefits of the Binance Crypto Pump Signals project is its accessibility and user-friendly nature. To gain access to the channel, individuals can utilize Telegram, a widely used and convenient platform for numerous traders. By utilizing this fast and dependable communication channel, users can receive real-time signals and promptly respond to fluctuations within the cryptocurrency market. Additionally, subscribers of this community can easily switch to their desired trading pair on the Binance exchange by simply clicking on the link provided within the Telegram channel post, ensuring added convenience.
The project developers employ cutting-edge techniques in data analysis and predictive analytics to handle a vast amount of coin-related information, exchange data, and other variables that impact price fluctuations. Utilizing the power of artificial intelligence, they construct prediction models that effectively pinpoint upcoming altcoin pumps with unrivaled precision.
An essential approach for forecasting the movements of altcoin prices involves scrutinizing technical indicators of cryptocurrencies, such as price charts, trading volumes, and support and resistance levels. These crucial data aid in identifying promising coins that are likely to experience pumps in the foreseeable future.

In addition, the project’s creators consider various other factors that impact the cryptocurrency market, including news releases, project announcements, trading volumes, and more. Through the utilization of sophisticated forecasting models, they are able to identify potential signals of upcoming price surges, which are then shared with traders and investors via the Crypto Pump Signals for Binance Telegram channel.
The key advantage of this project lies in its incorporation of cutting-edge technologies, such as artificial intelligence and big data analysis, to generate the most precise and dependable signals about impending price surges. This enables traders and investors to stay ahead of the market and generate substantial profits in the short term by leveraging the information regarding forthcoming altcoin price surges for trading on the Binance exchange, both in BTC and USDT pairs.
All the necessary information can be found in the Telegram channel “Crypto pump signals for Binance” without any charge. To begin, you must subscribe to the channel and explore its contents, as it is the place where you will find regular updates on pumps happening on the Binance exchange at no cost. It is not necessary for users to have extensive trading experience or expertise in cryptocurrencies as all trading operations are automated. Traders will receive pre-made signals and recommendations for trading.
Thanks to the combination of artificial intelligence capabilities and technical resources, the project’s creators ensure the highest level of accuracy in forecasting and provide users with convenient tools for successful trading on the Binance exchange.
Why do you need cryptocurrency trading signals and price growth forecasts?
Crypto Pump Signals for Binance utilizes artificial intelligence (AI) to provide innovative cryptocurrency signals. By leveraging AI, this platform can analyze vast amounts of data and accurately predict trends in the crypto market.

There are several advantages to using cryptocurrency trading signals:
- Well-informed choices: Traders and investors are equipped with current market information through signals and forecasts of altcoin price dynamics, enabling them to make well-informed choices when purchasing or selling cryptocurrency.
- Time efficiency: The automated process of analyzing data and providing signals helps save time in studying the market and identifying opportune moments for pump.
- Risk reduction: Cryptocurrency signals and price movement predictions assist traders in anticipating potential price fluctuations or trends, thereby minimizing risks and dump scenarios.
Utilizing cryptocurrency signals can enhance the odds of flourishing in trading and investing in the crypto market. Stay informed with the latest trends and make well-informed choices with the assistance of the Crypto Pump Signals project for Binance, which tackles well-known obstacles that impede successful trading:
- 1. Unforeseeable nature of the market. The crypto market is renowned for its extreme volatility and unpredictability. This poses difficulties for traders who struggle to determine the opportune moments for buying or selling assets to generate profits. Crypto Pump Signals leverages AI to assess various factors and historical data, enabling the prediction of future market trends. This empowers traders to make educated decisions, thereby reducing the risk of losses.
- 2. The cryptocurrency market is constantly inundated with an overwhelming amount of news, updates, and changes, leading to information overload. This flood of information can make it challenging for investors and traders to make well-informed decisions. However, Crypto Pump Signals solves this problem by filtering and analyzing information from multiple sources and providing specific signals for buying or selling assets. This not only saves time but also simplifies the decision-making process.
- 3. Trading in the cryptocurrency market can be a daunting task, especially for beginners who lack experience and knowledge. Navigating the complexities of trading and predicting trends can be overwhelming. Thankfully, Crypto Pump Signals offers a solution by providing signals and recommendations that are backed by complex algorithms and data analysis. By relying on these signals, beginners can reduce the risk associated with trading and ensure successful trades.

Advantages of using the Crypto Pump Signals for Binance Telegram channel:
- There are multiple benefits to utilizing data from the Telegram channel Crypto Pump Signals for Binance, whether you’re a novice or an experienced trader:
- Receive precise predictions about upcoming altcoin pumps: Gain access to top-notch forecasts and analytics that will enable you to make lucrative trades in the cryptocurrency market on a daily basis.
- Timely information: By subscribing to the private Telegram channel, you can access pump signals ahead of other traders and take advantage of cryptocurrency price fluctuations.
- Save Time: By utilizing artificial intelligence, you can save valuable time and energy that would have otherwise been spent on independently analyzing the cryptocurrency market and making financial decisions.
Don’t let these advantages slip away – take advantage of them and enhance your chances of success in the realm of cryptocurrency trading!
Functionality of the Telegram channel “Crypto pump signals for Binance”
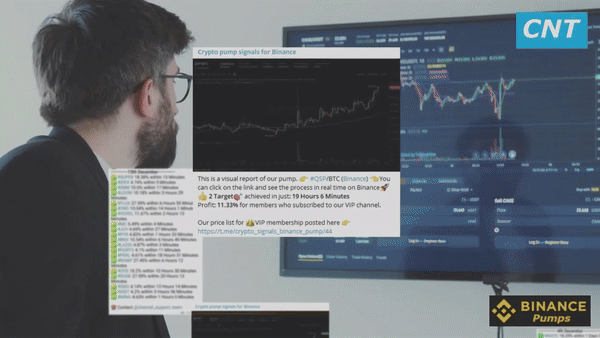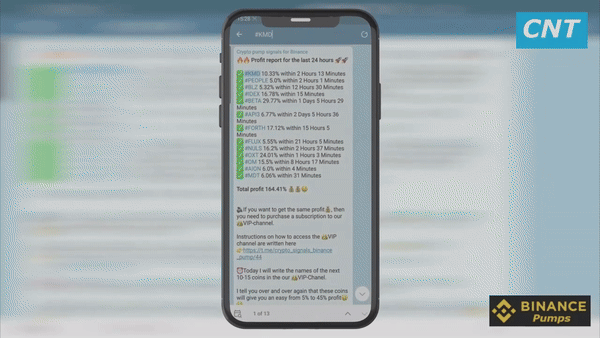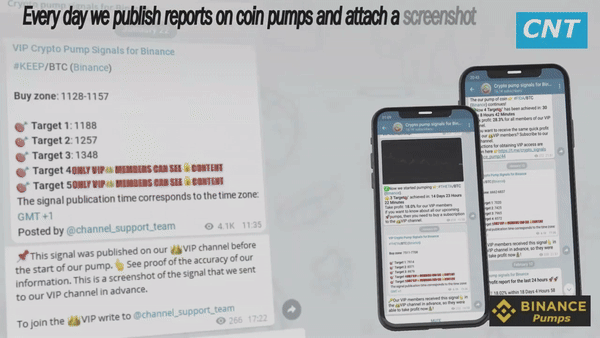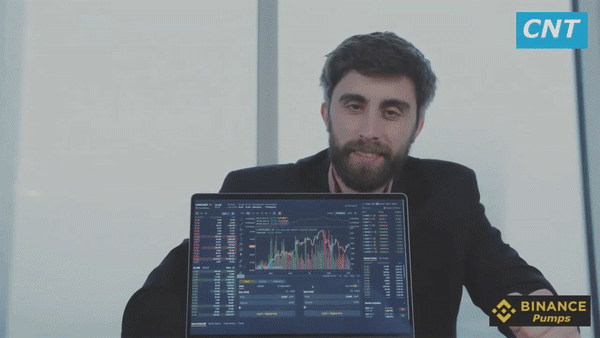
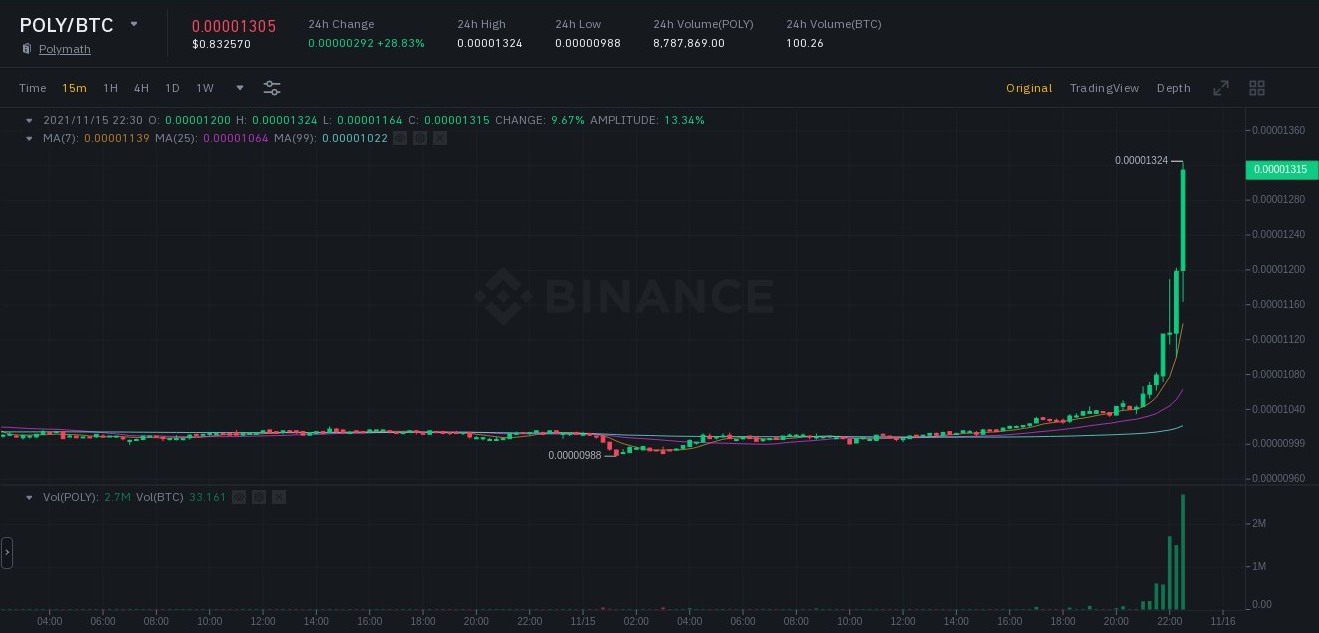
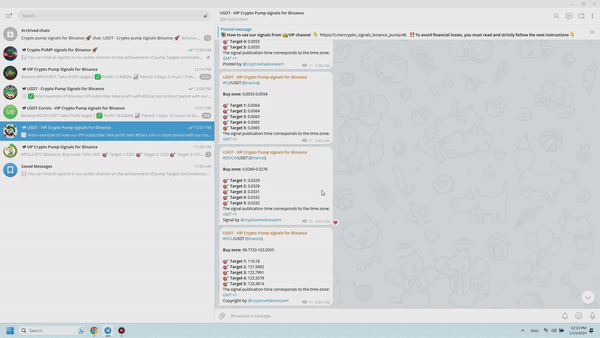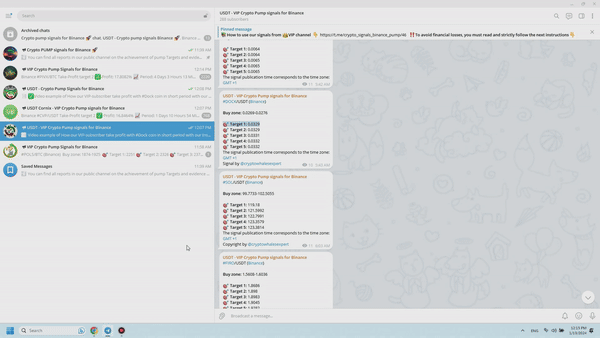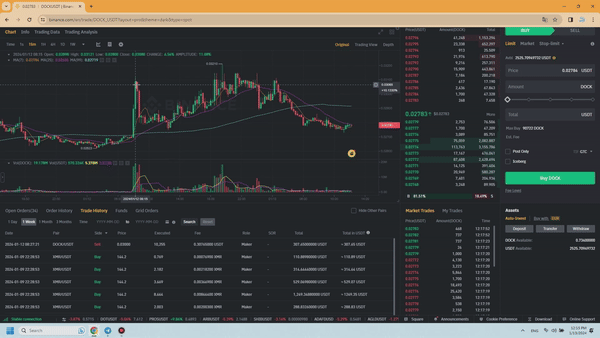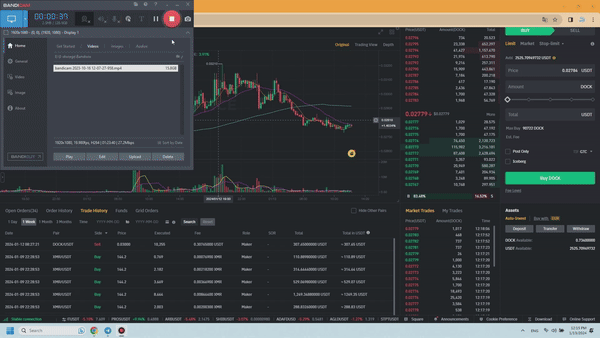
Imagine you have subscribed to a public channel called “Crypto pump signals for Binance” and you are struggling to comprehend the charts and images being shared. Now, I will provide an explanation of the primary content of the Telegram channel: it primarily consists of posts featuring screenshots displaying the fluctuation of prices of various cryptocurrencies. These screenshots showcase the price changes of digital coins that participants in the VIP channel have invested in and successfully profited from via “pump trading signals”. Within the published screenshots, you will find a series of consecutive stages showcasing a pump, which refers to sudden and significant increases in the value of a cryptocurrency. These price surges are represented by tall green candles on the chart.

Following each chart, data is released concerning the percentage of initial cost that subscribers to the VIP channel have profited. Additionally, the name of the currency pair and the duration of the “Pump” from the time the signal was posted in the VIP channel are provided, along with the ordinal number of the pump to indicate the investors’ achieved goal.
Once a pump has been completed and reported in the Telegram channel, a screenshot from the VIP channel is simultaneously published to prove the “accuracy of the pump signal data”. Verification is effortless. The post includes the time and date of the trading signal announcing the upcoming price rise of the specified coin.
By clicking on the link provided in the article, you will be directed to the Binance exchange’s platform, where all the important activities are taking place. Here, you can compare the starting time of the market’s sudden upsurge with the time when the signal was published. This is the reason why VIP channel subscribers can effectively benefit from such valuable information, which is essential for every cryptocurrency trader.
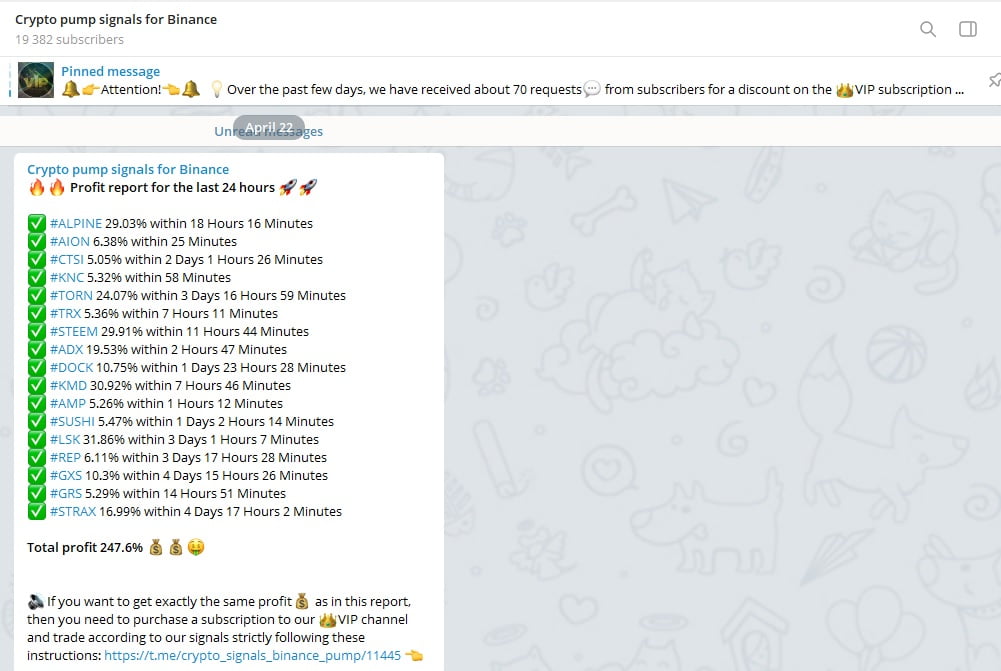
Furthermore, updated data regarding earnings generated from trading with “pump signals” is released every 24 hours. Typically, in the previous 24-hour period, subscribers of the VIP channel achieve a combined profit ranging from 100% to 180% of the initial entry price for cryptocurrency trades based on signals provided through the Telegram channel (this encompasses the total profit from all coins involved in the recent pump). This is precisely the purpose of the VIP channel – if you have entered the world of trading with the intention of making substantial profits, it is imperative that you gain access to it, regardless of any obstacles.
Now you have a grasp of how the free channel functions in the Telegram messaging app, as well as the upcoming crypto pumps and VIP channels provided by the ‘Crypto pump signals for Binance’ investor team. The public channel showcases proof of the investor team’s exceptional performance in delivering cryptocurrency pump signals. The primary activity takes place in the VIP channel, where subscribers generate profits, and receive real-time updates on the coins involved in trading. This includes recommended buy-in price levels and sell-off price ranges to maximize earnings from pre-purchased tokens. However, we will delve into this topic in more detail later on.
With the latest project update, it is now possible for individuals to earn money with minimal investment. The Telegram channel administrators have introduced a new feature where users can receive free signals about upcoming cryptocurrency pumps. This means that anyone can now utilize these signals to grow their capital and generate extra income. Each signal published in the community guarantees profit during the initial stage of the pump for the specified crypto currency pair mentioned in the signal. The time it takes to reach the first target of altcoin pumps can vary from one hour to two days. You can personally verify this without having to invest your own funds. Simply observe the reports published in this Telegram community. While it may initially sound too good to be true, these signals are proven to be effective and consistently bring profit to traders.
Below is a concise guide on utilizing complimentary signals:
Upon receiving a notification regarding a new signal in the Telegram channel “Crypto Pump Signals for Binance,” it is imperative to promptly acquire the designated coin within the price range denoted in the “Buy Zone” line. Subsequently, it is crucial to expeditiously execute a sell order for said coin on the Binance exchange at the price specified in the “Target 1” line and patiently await the fulfillment of your sell order, thus guaranteeing your profit.
How to use the VIP channel “Crypto pump signals for Binance”
There are two sections in the Crypto Pump Signals for Binance project. The first one is a public channel, where information, reports, and profit statistics are shared for free. The second section is a VIP section, which is only accessible to subscribers who have paid a membership fee. In the VIP section, more accurate signals about upcoming coin pumps are published.
- Traders in the public channel can verify the accuracy of the signals from the VIP channel by using “proofs” that are simultaneously shared with reports on ongoing pumps. The Telegram channel posts include screenshots of signals from the VIP channel, displaying recommended coin price values at the entry point of the trade and five pump targets with exit points.
- The VIP channel posts signals that traders can use to predict market movements and make profits in the coming days or even hours. Additionally, this private channel provides information on future targets for altcoin pumps, allowing traders to determine how much a coin’s price is expected to rise in the near future.

Therefore, Crypto Pump Signals for Binance offers traders and investors the chance to receive timely and accurate signals about upcoming altcoin pumps in a Telegram channel, as well as verify the accuracy of forecasts through “proofs” that are published simultaneously with reports of achieving pumping goals for digital coins. This enables traders to make informed decisions and utilize this information for trading in order to generate quick profits.
What are “signal proofs” and how do they help verify the accuracy of information?
The proofs are posted as soon as a coin pump is reported. The screenshot shows the mentioned coin from the VIP channel signal and indicates whether any of the five potential pump targets have been reached. The exit points for future pump targets are blurred for security, but there is always one pump target open in the near future, providing users with information on the expected price increase.
By utilizing data from proof posts, traders can gain an edge and leverage this information for their trading activities with the goal of attaining swift profits. They can easily validate the precision of signals from the VIP channel by comparing them against the actual results showcased in the “proofs.” This empowers users to make well-informed decisions and mitigate risks.

Now that you have already acquired the skills to analyze information in the public channel, it is an ideal moment to acquaint yourself with the VIP channel and its trading features on the exchange.
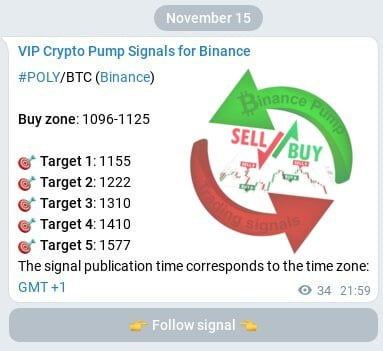
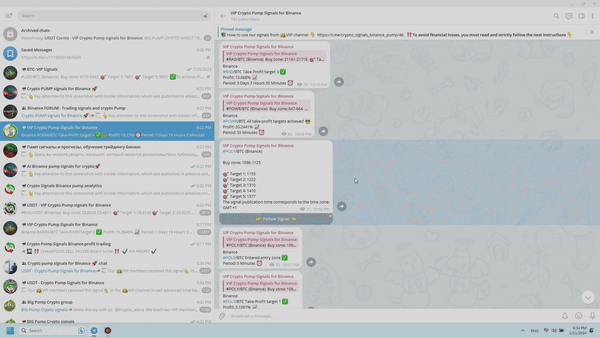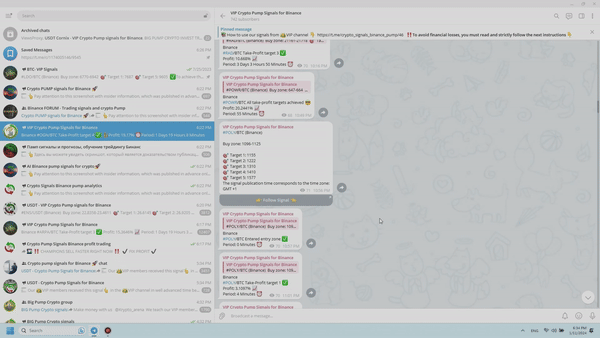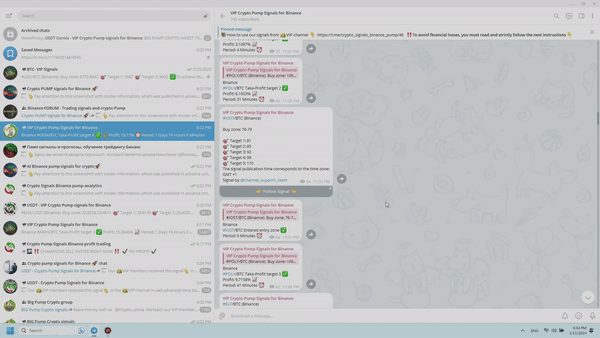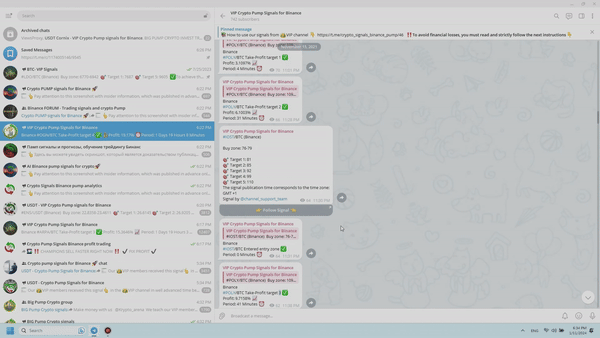
The main concept of the premium group’s operations on the Telegram app can be easily understood: upon purchasing a VIP subscription, you will receive an invitation link that will allow you to join a channel where you will gain exclusive insights on the digital currencies that the “Crypto pump signals for Binance” trading team will be working with. Let’s delve into a comprehensive plan regarding the signal work for successful cryptocurrency trading. In order to illustrate this, let’s examine a real example of a trading signal that occurred on November 15.
Therefore, upon receiving a notification regarding a new message in the VIP channel on Telegram, you will be presented with a signal on your screen regarding an impending surge in a specific cryptocurrency on the Binance exchange.
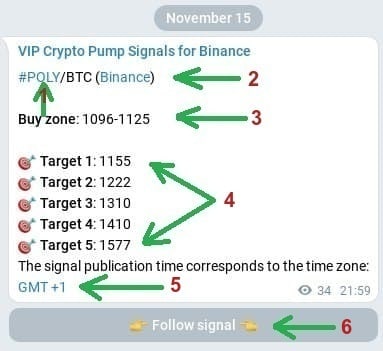
Firstly, let’s review the conventions utilized in the “pump signal” message:
- Initially, we come across the name of the Telegram channel, which requires no explanation.
- Following that, there is a hyperlink in blue color with the text #POLY/BTC (Binance). Interpret this line as follows: POLY/BTC indicates the coin’s name in the pair with Bitcoin, meaning you should purchase the “POLY” token. It is now apparent to everyone that Binance is the exchange where this coin is listed in the trading signal. For your convenience, there is a direct link in the word Binance that takes you to trading with the mentioned coin.
- The recommended price range for buying the digital coin within this signal is 1096-1125. This range guarantees profit once the first target of the upcoming pump is reached.
- One crucial part of the signal post is the final section which presents exit points named as target 1-5. These targets represent the future price levels at which it is advisable to sell the digital token. For instance, if you prefer quick profits, you can sell all your previously bought volumes of this asset once the first target value specified in the trading signal is achieved. If you are willing to wait for a higher return, set sell orders at the subsequent pump targets and wait for them to be reached. Typically, this waiting period lasts anywhere from a few minutes to several days.
Below, you can find a visualization of the outcome of a triumphant coin pump as indicated in the signal. This specific instance exemplifies that the initial three pump objectives were accomplished in under 60 minutes, resulting in an 18% gain for VIP members of the “Crypto Pump Signals for Binance” Telegram channel. Naturally, you too have the potential to attain comparable success in cryptocurrency trading by acquiring a premium subscription.
- The first step is to receive a signal in the VIP channel.
- Purchase the “coin mentioned in the signal” within the recommended price range.
- Set up sell orders at the values indicated in the “Target 1 – Target 5” lines.
- Sit back and enjoy the profit after a short waiting period.
Executing these steps is remarkably straightforward, and now you comprehend the simplicity of making money through VIP club membership. This is because the private VIP channel “Crypto Pump Signals for Binance” on Telegram caters to individuals seeking to consistently secure substantial profits swiftly and frequently. VIP subscribers earn significantly higher income than regular traders who lack such privileged information. Furthermore, by watching this video presentation, you will not only gain a stable income but also acquire new knowledge and genuine trading experience on the immensely popular Binance exchange.
Every trader who bought subscription to any type of VIP channel has the opportunity not only to make a profit using accurate signals about the upcoming coin pump, but also can get absolutely free access to a higher-level VIP channel!
To do this, you just need to record the screen so that the video clip clearly shows the signal you received from the VIP channel that you used for trading and, accordingly, the closed deal as a result of using this signal. Send the video you recorded to the channel administrator and receive an invitation link to VIP channel of a higher level to use more profitable signals within 1 month completely free. Here is an example of a video recorded by a subscriber with a “Silver” subscription type to a VIP channel intended for trading coins paired with USDT, pay attention to the date and time the signal was received and when the #DOCK coin was sold.
Furthermore, there are several exclusive deals available on the Telegram channel “Crypto pump signals for Binance” for highly engaged individuals. Let’s take a closer look at them.
It is understandable that a VIP subscription may be costly and not accessible to everyone. However, as a proactive follower, you have the opportunity to enjoy a substantial discount on any VIP subscription or even have a chance to obtain it for free. These promotions specifically cater to the active members of the Telegram channel.
In order to receive a customized discount, it is necessary to encourage your acquaintances to join the complimentary Telegram channel: for every referral you bring in, you will receive a 2% reduction on the overall price of a VIP subscription. All you have to do is transmit the roster of your referrals to the channel administrator and take into account that “the discount is already in your possession,” but bear in mind that the maximum amount for the superior subscription, discount included, should not surpass 50%.
Every Sunday, there is a weekly giveaway for a free VIP subscription to an exclusive group of traders. In order to enter the giveaway, you must invite a friend to join the Telegram channel called “Crypto pump signals for Binance” and provide their name to the support service administrator. Once the automated system verifies the new subscriber, your account will automatically be entered into the drawing. It is important to note that every week, three winners will be randomly selected to receive an invitation link to the secret channel. This channel provides insider information about upcoming “pumps” for specific digital tokens paired with the dollar or bitcoin.
By now you are already aware of the purpose of these Telegram channels: they have been established by a group of traders known as Crypto pump signals for Binance, and you have the opportunity to subscribe to them at this moment. At this point, you have gained the knowledge on how to effectively utilize these channels in order to generate profits through “pump signals.” Furthermore, you have grasped the concept of acquiring an additional discount on a VIP subscription, as it is the only way to attain significant profitability when engaging in cryptocurrency trading. This team of traders also maintains a YouTube channel where several instructional videos are available, guiding you on how to safely earn money by leveraging insider information pertaining to forthcoming cryptocurrency pumps occurring on the Binance exchange.
Strategy for using signals posted in the VIP channel
This guide is designed for traders who are interested in learning how to interpret, comprehend, and utilize trading signals provided by the “Crypto pump signals for Binance” VIP channel from an investor team. To prevent any potential financial losses, it is crucial to thoroughly read and strictly adhere to the instructions outlined below:
- 1. As soon as you receive a notification regarding a new signal in the VIP channel, it is imperative to purchase the specified coin immediately within the designated price range mentioned in the “Buy Zone” section. Following this, proceed to promptly place sell orders for the coin on the exchange at the prices stated in the lines encompassing “starting from Target 1… up to… Target 5 inclusive.” Subsequently, it is necessary to wait for the orders to be executed on the Binance exchange, ensuring the realization of profit.
- 2. Solely utilize the most recent signals that have already been disseminated in the Crypto Pump Signals VIP channel specifically tailored for Binance. To optimize financial gain and minimize risk, we recommend dedicating no more than 3-5% of your total capital to each coin.
- 3. It is strongly advised to refrain from investing all of your capital into a single coin or a small number of coins. To maximize profit and minimize wasted time, it is recommended to invest in a minimum of 3-4 new coins daily. This practice is essential as it accounts for the fact that a coin may not reach at least the first target for an extended period of time. Based on statistics, this timeframe can range from one hour to several days upon receiving the signal in the VIP channel. Moreover, it is crucial to acknowledge that each published coin may participate in a pump during different time periods, depending on the current cryptocurrency market conditions.
- 4. The VIP channel Crypto Pump Signals for Binance is already synchronized with the @cornix_trading_bot. This integration enables the use of automated trading on Binance. If you observe the presence of the “Follow signal” button below each post in the exclusive VIP channel, simply click on it and follow the instructions provided by the assistant bot to configure automated trading via the Cornix bot.
Watch this a video tutorial how to use and setup Cornix bot for automatic tradings.
The impact of subscription prices on the VIP channel based on tariff plans
The project Crypto Pump Signals for Binance offers a range of paid subscription options designed to cater to the diverse needs of cryptocurrency traders seeking profitable trading signals:
Watch video: How to subscribe to the any VIP channel of “Crypto Pump Signals for Binance” project in Telegram and what types of subscriptions exist.
- The “Light” plan provides subscribers with access to signals indicating upcoming cryptocurrency pumps, generated by artificial intelligence, for use on the Binance exchange. While these signals are reliable and accurate, they may not offer the same level of precision and speed in achieving pump targets as the higher-level plans. This subscription option is ideal for traders who wish to familiarize themselves with the service at an affordable cost.
- The “Bronze” subscription tier provides access to more advanced algorithms and machine learning models designed to generate highly precise and current signals regarding significant spikes in cryptocurrency value. This subscription ensures that subscribers receive signals about coins with the potential for a “crypto pump” in the near future as quickly as possible, enabling faster attainment of the preset pump targets. The “Bronze” plan is ideal for traders seeking to optimize profit potential by receiving highly accurate signals and achieving predicted results promptly.
- The “Silver” subscription option is the next tier of signal quality following the “Bronze” subscription. It grants subscribers access to an exclusive VIP channel for receiving more precise and expedited signals regarding upcoming cryptocurrency “pumps” in the near future from our advanced artificial intelligence system. With this pricing plan, traders will have the opportunity to achieve the majority of the outlined objectives in the signal ahead of other subscribers with “Lite” or “Bronze” plans.
- The “Gold” tariff plan provides an even higher level of precision and efficiency in achieving the majority of artificial intelligence-generated pump signals. Those traders who subscribe to this plan can anticipate reaching all five “pump targets” much earlier compared to those who are subscribed to the Light, Bronze, or Silver plans. The Gold plan is tailored to traders who seek maximum accuracy and speed in gaining profits from cryptocurrency trading. Furthermore, from the Gold subscription tier onwards, traders have the opportunity to utilize the automated trading bot, Cornix. This allows for profit maximization and eliminates the necessity for manual trading. The bot scans all received Telegram channel signals and employs this information to enter and exit trades as soon as the asset price hits the target price specified in the five “pump targets”.
- The “Platinum” subscription is the advanced tier of subscription and offers even more precise and quicker signals regarding cryptocurrency pumps generated by artificial intelligence. Traders opting for this package can anticipate receiving information regarding coins with the potential to hit all five pump targets before those subscribed to the “Lite”, “Bronze”, “Silver”, and “Gold” plans. This particular subscription type is indefinite, freeing subscribers from the hassle of needing to renew their subscription indefinitely. Platinum subscribers gain entry to various VIP channels where signals for both manual trading and the automated trading bot “Cornix” are posted, in addition to a VIP channel containing signals for trading cryptocurrencies paired with USDT; this enables more efficient and convenient trading using a stable and dependable cryptocurrency.
- The “Premium” tariff plan is the top-tier option in the subscription hierarchy, offering subscribers access to a channel where artificial intelligence generates highly profitable and fast signals known as “pumps”. Subscribers to this plan will receive VIP signals about upcoming coin pumps that have the highest likelihood of hitting all five pump targets in the short term, surpassing any other lower-level subscriptions. Additionally, this plan includes the perk of priority support from a dedicated personal manager.
- Exclusive offer for new traders: Gain entry to two exclusive trading channels for BTC and USDT coin pairings by paying just 30% of the yearly subscription fee for the Gold VIP subscription. However, to complete the payment, you must utilize the “signals” from these VIP channels within 30 days and cover the remaining portion of the subscription fee.
This opportunity will enable you to exponentially grow your wealth within a brief timeframe and witness the caliber of the data provided in the exclusive channels!
Generally speaking, VIP subscribers receive exclusive notifications about upcoming coin value increases on a daily basis through a private Telegram channel. This implies that once you purchase a subscription, you will gain access to information that is only accessible to a select group of privileged traders.

But there is more to it! The number of Pump targets that are achieved within the next 24 hours after the signal is shared for each coin increases with each premium tariff plan. This opens up additional opportunities for you to profit from cryptocurrency trading. In other words, with a higher-priced plan, you can earn profits at a faster and larger scale using these trading signals while having a high level of confidence in their accuracy.
Take, for instance, Traders who possess a lifetime Platinum VIP subscription. They achieve a remarkable feat by successfully hitting all five Pump targets for every coin released in the Platinum VIP channel in the immediate future. The likelihood of this success stands at no less than 98%, offering them the opportunity to generate significantly higher profits in terms of percentage per month compared to those with lower-tier subscriptions.
What’s even more fascinating is that the accuracy and speed of the signal in the short term (within 1 hour to 48 hours from the moment of signal publication in the VIP channel) varies from 84% to 98% depending on the type of subscription. It means that you can swiftly respond to market fluctuations and maximize your earnings.
Furthermore, the greater the tariff plan, the larger the percentage of profit you will receive for each signal that is successfully triggered. And it’s important to keep in mind that your subscription duration also impacts your potential to earn more: the higher your subscription level, the longer the validity period!
Therefore, don’t pass up the chance to join the exclusive community of traders and begin earning significantly more by utilizing the trading signals concerning the anticipated rise of cryptocurrency from the venture “Crypto PUMP signals for Binance”!

Why did we not now providing free signals from our VIP channel?
Artificial intelligence is crucial in the analysis and processing of vast amounts of data that are utilized for the creation of trading signals for various pricing plans. This technology harnesses sophisticated algorithms and machine learning models to scrutinize market trends, news updates, historical data, and an array of other factors.
Artificial intelligence has the ability to adapt to market conditions that are constantly changing and update its recommendations in real-time. This technology has proven to be extremely beneficial for traders in achieving their financial goals and increasing their success in financial markets. It does this by providing them with the most profitable opportunities available.
However, the administration behind the “Crypto PUMP signals for Binance” project has decided to discontinue the provision of free signals and free access to the VIP channel for a number of reasons:
- Firstly, the team of investors puts forth substantial financial resources for the organization and execution of coin “pumps”.
- Secondly, certain VIP subscribers and investors contribute their own funds to support the development of VIP channels and for server maintenance purposes.
In order to become a member of our exclusive VIP subscribers club, a membership fee must be paid by all new participants. In the past, we used to share screenshots of our VIP channels with everyone and even provided free samples of our signals as a way to demonstrate their quality and reliability. However, due to a significant number of individuals who took advantage of this by either using the information for their own personal gain or reselling the signals, we have decided to discontinue this practice.
In addition, our Support Team receives a high volume of messages from various individuals and does not have the capacity to distribute free signals or provide answers to questions that are already addressed in the channel instructions posted in the channel messages.
If you are genuinely interested in receiving pump signals, it is recommended to consider subscribing to the most affordable plan. This is a common practice even among our competitors. For professional traders who rely on pump signals to trade on Binance, this should not pose any issue. Below are some examples of free signals that have yielded profitable results for our VIP subscribers.
To ensure transparency and verify the accuracy of all coin signals published in our exclusive VIP channel before a pump commences, we provide comprehensive reports in our public channel. We encourage you to thoroughly review and analyze this information.
Affiliate Program: Invite Traders and Get Rewarded to Your BTC Wallet
Get your friends and any traders to subscribe to the Crypto Pump Signals VIP channel for Binance and earn rewards. Essentially, you can offer anyone on social media or freelance platforms the chance to purchase a VIP subscription to the Crypto Pump Signals VIP channel for Binance at a guaranteed 10% discount, and you will receive a generous commission as a reward! This is a win-win situation for both the buyer of the VIP subscription and yourself!
Once your invited friend joins the VIP group, you should provide the following information to the channel administrator:
- The name of the person you invited and a link to their TELEGRAM profile (e.g., @your_friend_username).
- Your Bitcoin wallet address for receiving the reward.
- The reward is calculated as 10% of the total cost of the VIP subscription purchased by the individual whom you referred.
- If you are able to attract more than 10 VIP subscribers in a month, there is an additional bonus of 5% added to your reward.
To summarize, if you can successfully invite more than 10 people in a month, your reward amount will be increased to 15% of the subscription cost paid by the person you referred.
How to get a personal discount on VIP subscription in the pump signals channel?
There is an exclusive promotion where you have the opportunity to determine the amount of the discount on the VIP subscription by yourself! The requirements to qualify for the discount are very straightforward:
- You introduce a friend who subscribes to the complimentary Telegram channel and automatically receive a 2% discount on any type of subscription for the VIP channel. The more friends you introduce, the larger the discount! Remember the primary rule, the discount cannot exceed 50% of the selected subscription price. If a majority of your friends unsubscribe within a month, you will lose half of the subscription period for the VIP channel Crypto Pump Signals for Binance. (Exception: lifetime subscription to the Premium and Platinum package).
- Submit the roster of friends who enlisted in the Telegram channel to the administrator: @cryptowhalesexpert
- Subsequently, you are entitled to purchase a VIP channel subscription at a significantly reduced price based on the following calculation: for every subscriber you refer, you will receive a 2% discount.
Reviews from traders about using the VIP channel “Crypto pump signals for Binance”
If you are still deciding whether to join our VIP channel, you can check out what traders are saying about our cryptocurrency pump signals in the comments below. Our subscribers are always satisfied because they can’t find such reliable and exclusive information anywhere else.
There are individuals who were not contented with their previous earnings and those who desired to embark on a new business who became channel subscribers. They acquired tokens and engaged in pumps based on signals from the Telegram channel. Every one of them earned up to 30% profit within the initial few hours of trading. Channel subscribers suggest subscribing to the VIP edition as it ensures profit, whereas the free channel only offers one or two signals each day.
You have the opportunity to dive into statistics and explore historical records of coin pumps, as well as estimate the magnitude of profit earned by participants of our VIP channel. To accomplish this, simply follow the link to our Telegram channel and select the specific year, month, and day of interest. The report will be displayed as a comprehensive list of coins, outlining their respective profit percentages and the duration of time it took to achieve the desired increase in value. For each coin on the list, you can authenticate the accuracy of the information by clicking on the “#” symbol preceding its name. This will open up a search field, allowing you to conveniently scroll upwards and locate the necessary details.

To maximize your gains from trading cryptocurrencies, it is necessary to prepay for a VIP subscription, though this payment will be refunded within 24 hours. By anticipating future price surges in digital tokens, you can ensure that your profits far outweigh the costs of the subscription. Additionally, if you refer a friend to subscribe to the VIP channel, you will be rewarded with a discount or possibly even a free subscription. Merely knowing when a new pump will occur is not enough; it is crucial to act appropriately during the pump to guarantee profitability.
Hence, we have discussed one of the most popular platforms for receiving free signals regarding cryptocurrency pumps. Crypto Pump Signals Binance delivers high-quality information about upcoming pumps on the Binance exchange, enabling investors to profit from trading digital tokens.
One of the main benefits of a service that offers precise forecasts for cryptocurrency prices based on artificial intelligence is its distinct advantages:
- Complimentary signals for cryptocurrency pumps.
- Unparalleled signal accuracy.
- 24/7 customer support.
- Simple and user-friendly interface.
- Instant notification system for prompt response to signals.
Join now a community of accomplished traders and generate income from trading digital tokens by utilizing reliable and top-notch pump signals from Crypto Pump Signals for Binance. Don’t pass up the opportunity to profit from cryptocurrency and become a successful investor.
How to get started trading cryptocurrency using forecasts, predictions, and trading signals?
If you’re looking to make money trading cryptocurrency but unsure of where to begin, trading signals could be the key to your success. These automated trading tools are gaining traction in the world of cryptocurrency trading, assisting traders in making profitable trades with minimal risk. What exactly are trading signals, and how can you access them? This guide will provide insight into the world of trading signals, explaining their benefits for both novice and seasoned traders.
What exactly are trading signals in the world of cryptocurrency? Crypto trading signals are alerts that notify you of opportune moments to purchase or sell digital coins. These signals also recommend which coins may offer the best returns on investment at a particular time. Trading signals for buying and selling provide traders with insights into potentially profitable transactions based on analysis.
Cryptocurrency trading signals are generated through meticulous forecasting of market conditions and are crucial for making informed decisions. However, obtaining precise and trustworthy data can be challenging when attempting to forecast independently. This is when inexperienced traders seek assistance from experts and seek guidance from trading signal platforms. Many of these platforms now utilize artificial intelligence trading signals, which simplifies the process of learning how to initiate trading activities in the realm of cryptocurrencies.
Cryptocurrency trading signals contain crucial data about potential price fluctuations of certain coins and perform analysis of the cryptocurrency market. These signals often involve forecasts derived from analytics.
The main advantages of utilizing signals for cryptocurrency trading are:
Automation: Cryptocurrency trading signals streamline the laborious tasks that many traders find burdensome, allowing users to save significant time. Users simply need to adhere to the instructions outlined in the crypto signal.
Exchange transactions often involve emotions, with traders often making decisions based on emotions rather than following a detailed plan. This is often due to the emotional burden involved. While this approach may occasionally result in success, it is not always the most effective strategy. However, by following a clear and logical strategy developed by a team of professionals, all doubts can be eliminated. The user simply needs to follow the guidance provided. This approach also helps to eliminate any stressful factors that may arise.
Cryptocurrency trading signals are essential in the market, appealing to novice and seasoned traders alike. These algorithms aid experienced traders in discovering fresh strategies and enable beginners to acquire valuable expertise in crypto trading. Signals automate trading activities, enhancing traders’ financial stability by mitigating potential losses and safeguarding against bankruptcy in the volatile crypto market.
How do trading signals work? Trading signals are usually produced by an automated system that uses technical analysis on the provider’s servers. When a profitable opportunity is found, you’ll get a notification through email, SMS, or social media with the recommended trade details. These signals can be connected directly to your trading platform, allowing you to execute trades without switching from your investment software.
Upon receiving a trading signal, you have the choice to follow the advice or not. Some traders might find the potential risks too great or prefer to do their own fundamental or technical analysis, which could lead them to question the signal’s effectiveness.
Automating your response and using an embedded program can help you reduce the delay between identifying precise trading signals and opening a position, potentially increasing profits. However, if you opt for automation, you need to be mindful that you won’t be able to disregard signals on a case-by-case basis.
You can customize the signals you receive by setting various parameters, such as specifying the assets for which you want notifications and setting limits on when to open positions. Day traders and scalpers might prefer signals on shorter timeframes like one or five minutes, while others may opt for hourly or eight-hour intervals on charts.
How can you interpret and make sense of trading signals? Reading cryptocurrency trading signals may seem daunting and require a basic grasp of the market and technical analysis. However, you can follow these straightforward steps:
- First, make sure to consider the entry price. This is the suggested price for buying or selling a specific cryptocurrency.
- Next, check the stop-loss price. This is the price at which you should close the trade if the market moves in the opposite direction. It is crucial for managing your potential losses.
- Also, pay attention to the take-profit price. Exit the trade to take profit at this price. Typically, the take-profit price is higher than the entry price.
- Additionally, analyze market sentiment. Trading signals often include market analysis to explain the rationale behind the trade. Understanding this analysis is essential for making well-informed decisions.
- Additionally, it is important to focus on technical analysis. Cryptocurrency trading signals often depend on technical analysis, which involves analyzing charts and patterns to predict market movements. If you want to dive deeper into technical analysis, do so.
- After you have placed a trade, it is vital to monitor it closely. Stay vigilant about the market and be ready to exit the trade if it goes unfavorably.
Remember that trading signals do not guarantee profits. It is still crucial to research and make your own choices. Nevertheless, cryptocurrency trading signals can assist beginners or those seeking to save time on market analysis.
How to receive trading signals? You can obtain cryptocurrency signals from different sources like Telegram, Twitter, TradingView, and forums. However, it is crucial to note that not all signal providers are trustworthy. Before opting for signals, conduct thorough research. It is also recommended to begin with modest sums and consistently mitigate risks through setting stop losses.
If you seek a dependable platform for trading signals, contemplate utilizing Binance trading signals. They can facilitate your trading choices grounded on profitability and likelihood.
We provide complimentary trading signals for cryptocurrency day trading upon registration, along with integrated risk management tools. For instance, each signal includes preset stop-loss and take-profit parameters that you can adjust as needed. Moreover, features such as “Multiplier” and “Auto Multiplier” offer the opportunity to increase your investment amount in favorable market conditions.
You can analyze trading signals from the Telegram channel “Crypto PUMP signals for Binance” to make informed trading decisions, test theories, and strategize trades based on insights from professional traders. These user-friendly signals help traders stay informed about market trends and execute trades in line with the current cryptocurrency market environment.
Moreover, the “Crypto PUMP signals for Binance” trading signals include Take Profit and Stop Loss options to assist in risk management. These signals can be accessed on any device, with an enhanced version available on the Telegram channel. The signals are automatically adjusted according to the current asset price, increasing their reliability.
Why does trading seem so complicated? Is it really? Trading can be intricate due to the multitude of factors involved. However, it can be simplified by recognizing profitable trading signals.
Trading signals encompass a wealth of potentially misleading information, personal biases, and the necessity to balance risk and reward. For a novice trader, deciphering what to prioritize may pose a challenge.
One of the reasons trading is so intricate is the prevalence of false information found on the web. Distinguishing between valuable recommendations and worthless content can prove challenging. To steer clear of the pitfalls of misleading trading advice, it is crucial to thoroughly test all strategies using backtesting software before engaging in actual trades.
Maintaining objectivity throughout the trading process is also essential. Many traders have a tendency to impose their own beliefs on the market, leading to potentially erroneous decisions. A reliable trading strategy plays a vital role in achieving success. A trading strategy consists of a set of rules that dictate the entry and exit points for trades, as well as the purchase and sale volumes without hedging. It should be clearly defined and preferably coded in a programming language for effective backtesting.
- Individual traders. Cryptocurrency trading signals are highly sought after by individual traders, both newbies and seasoned investors, looking to make more informed decisions regarding the buying and selling of cryptocurrencies. These signals offer valuable insights into potential market trends, enabling traders to exploit opportunities.
- Day traders. Day traders specialize in short-term trading, executing buy and sell orders of cryptocurrencies within a single trading day. They rely on trading signals to pinpoint intra-day opportunities and profit from price fluctuations.
- Swing traders. Swing traders seek to capitalize on price swings over several days or weeks. Trading signals assist them in determining optimal entry and exit points through technical or fundamental analysis.
- Hedge funds and institutional investors. Some hedge funds and institutional investors participating in cryptocurrency trading use signals as part of their overall trading strategy. These signals can be generated by algorithmic trading systems or their own analysts.
- Algorithmic traders. Traders using automated trading algorithms or trading signal bots may incorporate crypto trading signals into their systems. Algorithms can execute trades based on predefined criteria derived from these signals.
- Crypto exchanges. Some cryptocurrency exchanges offer trading signals or analysis tools to their users. Traders on these platforms may access signals to make more informed trading decisions.
- Signal providers. Some individuals and organizations specialize in providing cryptocurrency trading signals as a service. These signal providers analyze the market and provide subscribers with trading recommendations for a fee.
- Investment advisors. Financial experts and investment consultants specializing in cryptocurrencies may use trading signals to assist their clients in making investment decisions.
- Long-term investors. Investors with a long-term perspective on cryptocurrencies can use signals to identify strategic entry points for accumulating assets or making adjustments to their portfolio.
- Educational Goals. Trading cryptocurrency signals can also be used for educational purposes. Traders, especially newcomers to the market, can use signals to understand how trading strategies are formulated and implemented.
Users should exercise caution and conduct thorough research on cryptocurrency trading signals. Markets can be volatile, and trading carries risks. Additionally, the quality and accuracy of signals may vary, so users should choose reliable sources and consider signals as part of the overall decision-making process.
Is it worth buying “Crypto PUMP signals for Binance” trading signals? The decision whether to invest in cryptocurrency trading signals depends on several factors, such as your level of trading experience and knowledge, the reliability of the signal provider, and your risk tolerance. For novice traders, cryptocurrency trading signals like “Crypto PUMP signals for Binance” can be a valuable tool to start their trading journey. However, it is crucial to conduct thorough research before choosing a reliable signal provider.
Tips and recommendations for effective use of Crypto Pump Signals
To optimize your use of Crypto Pump Signals on Binance and maximize your profits, it is advisable to adhere to certain tips and strategies. Here are a few:
- Thoroughly analyze the signals: Prior to utilizing a signal, take the time to thoroughly review its description, analysis, and forecast. Ensure that you have a comprehensive understanding of the suggested trade and how sound the approach is. This will enable you to make an informed decision.
- It is advisable to set a stop-loss, regardless of how confident you may be in the signal’s success. A stop-loss level should be established to determine when you are willing to close your position in order to minimize potential losses. This practice will protect your capital and help manage risks effectively.
- It is essential to control your emotions when dealing with coin pumps, as they can be extremely volatile and emotionally challenging. Keeping your emotions in check and avoiding emotional outbursts is recommended. Stay committed to the strategy you have developed and have confidence in your decisions, which should be based on thorough analysis and information provided by the signals.
- For risk reduction and increased chances of success, it is advisable to diversify your portfolio by spreading your investments across various coins and markets. Relying solely on one signal or one coin is not recommended. Having a diverse range of assets in your portfolio is crucial for long-term profitability.
- Stay updated regularly: The cryptocurrency market is in a constant state of flux, with news, events, and trends having a profound impact on coin prices. It is highly recommended that you stay informed about the latest news, stay abreast of any updates, and consistently educate yourself in order to be prepared for any changes and adjust to market conditions.
By adhering to these guidelines, you can enhance your likelihood of success in utilizing Crypto Pump Signals and effectively manage your crypto portfolio. However, it is important to remember that investing in cryptocurrencies always carries a certain level of risk, and decisions should be made with your own responsibility in mind. Exercise wisdom and caution, and don’t forget to conduct your own analysis and research to make well-informed decisions.
How does the Crypto Pump Signals for Binance project work and where do signals about upcoming cryptocurrency pumps come from?
Crypto Pump Signals for Binance is an ingenious initiative that employs advanced AI technologies to analyze and forecast market trends in the cryptocurrency sector. This algorithm, trained on an extensive amount of data, has the capability to anticipate price fluctuations in cryptocurrencies, functioning as a personal analyst for traders subscribed to the VIP channel.
The operation of the intelligent system involves the following stages:
1. Gathering data: AI examines historical price data, trading volumes, news materials, and social signals to create a comprehensive market overview and construct a training database.
2. Preparing the data: The information is cleansed of unnecessary noise and structured into a suitable format. This stage is crucial as the quality of input data directly impacts the accuracy of forecast signals for traders.
3. Training the AI model: A variety of machine learning algorithms are utilized. Regression is employed to forecast prices, classification is used to determine the type of pump, and clustering is implemented to group similar pump features.
4. Testing the AI model: The model is assessed on new data that was not used during training to evaluate its ability to predict actual price fluctuations, and it achieves an accuracy of over 95%, as demonstrated by practice. This can be easily verified by analyzing reports on completed pumps published in the Telegram channel, along with evidence from the VIP channel.
5. Optimizing the AI model: If unsatisfactory testing results occur, the model is optimized by adjusting parameters or employing alternative machine learning methods.
6. Deploying the model: After successful testing and optimization, the model begins to operate in real-time, analyzing new data and issuing signals about upcoming pumps in the near future.
7. Monitoring and updating the model: The model is continuously monitored and updated as new data arrives and market conditions in the cryptocurrency industry fluctuate.
Crypto Pump Signals for Binance is an exceptional project that harnesses the power of artificial intelligence and machine learning to predict future cryptocurrency “pumps.” This cutting-edge solution can serve as a potent instrument in the hands of experienced traders and newcomers.

Utilizing intricate artificial intelligence algorithms, the Crypto Pump Signals project gathers and evaluates an extensive amount of information, including historical price data, trading volumes, news, and social signals. This facilitates a comprehensive market analysis and the establishment of a training database for AI.
In order to ascertain the likelihood of a pump for each cryptocurrency on the exchange in the near future, AI employs various mathematical models. For instance, regression techniques enable price prognostication, classification algorithms determine the type of pump, and clustering methods group similar attributes of forthcoming coin pumps together. Mathematical models of artificial intelligence such as “random forest,” gradient boosting, or neural networks are specifically employed for this purpose.
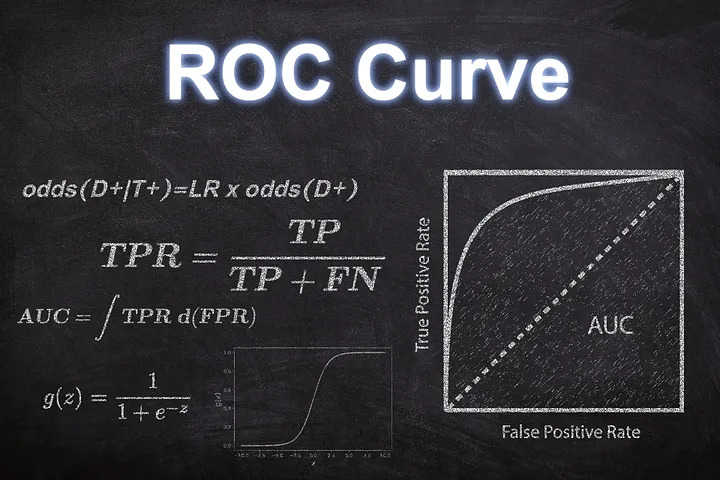
There are two approaches utilized for assessing signal precision: Pearson correlation and ROC curve. Pearson correlation gauges the extent of correlation between forecasted and real prices, whereas the ROC curve appraises the model’s classification proficiency.

In order to calculate the potential percentage increase in the price of every coin during a pump, AI employs statistical methodologies and time series forecasting algorithms. Models like ARIMA, LSTM, or Prophet are effectively utilized to accomplish this objective. They analyze historical price fluctuations and generate forecast signals about future price fluctuations for each coin on the exchange.
When it comes to determining the optimal timing for selling an asset and maximizing profit, AI uses a risk management and exit strategy approach. This entails establishing take-profit thresholds based on projected volatility and the potential percentage growth of the coin.